[Infographic] Mitigating Common VoIP Security Threats
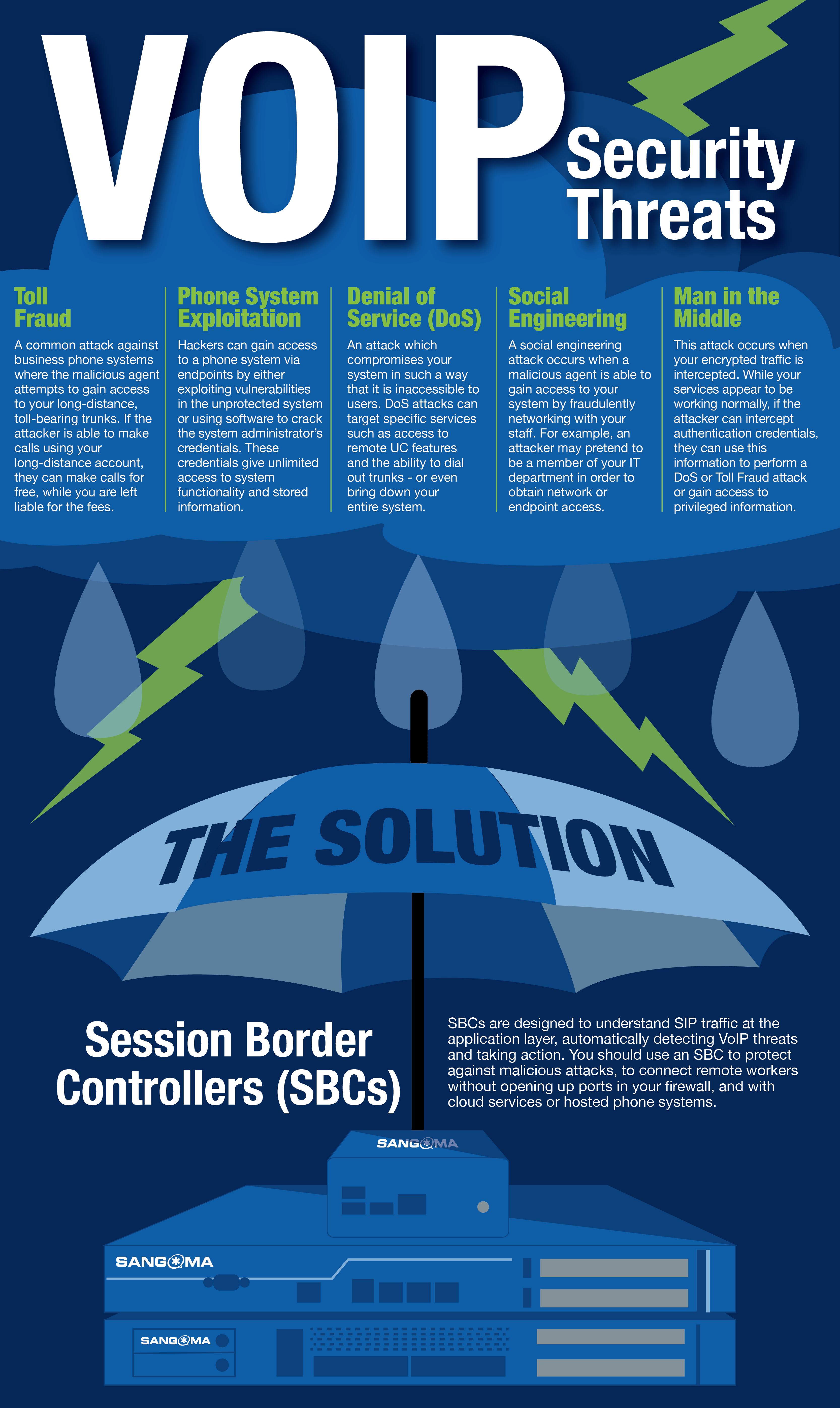
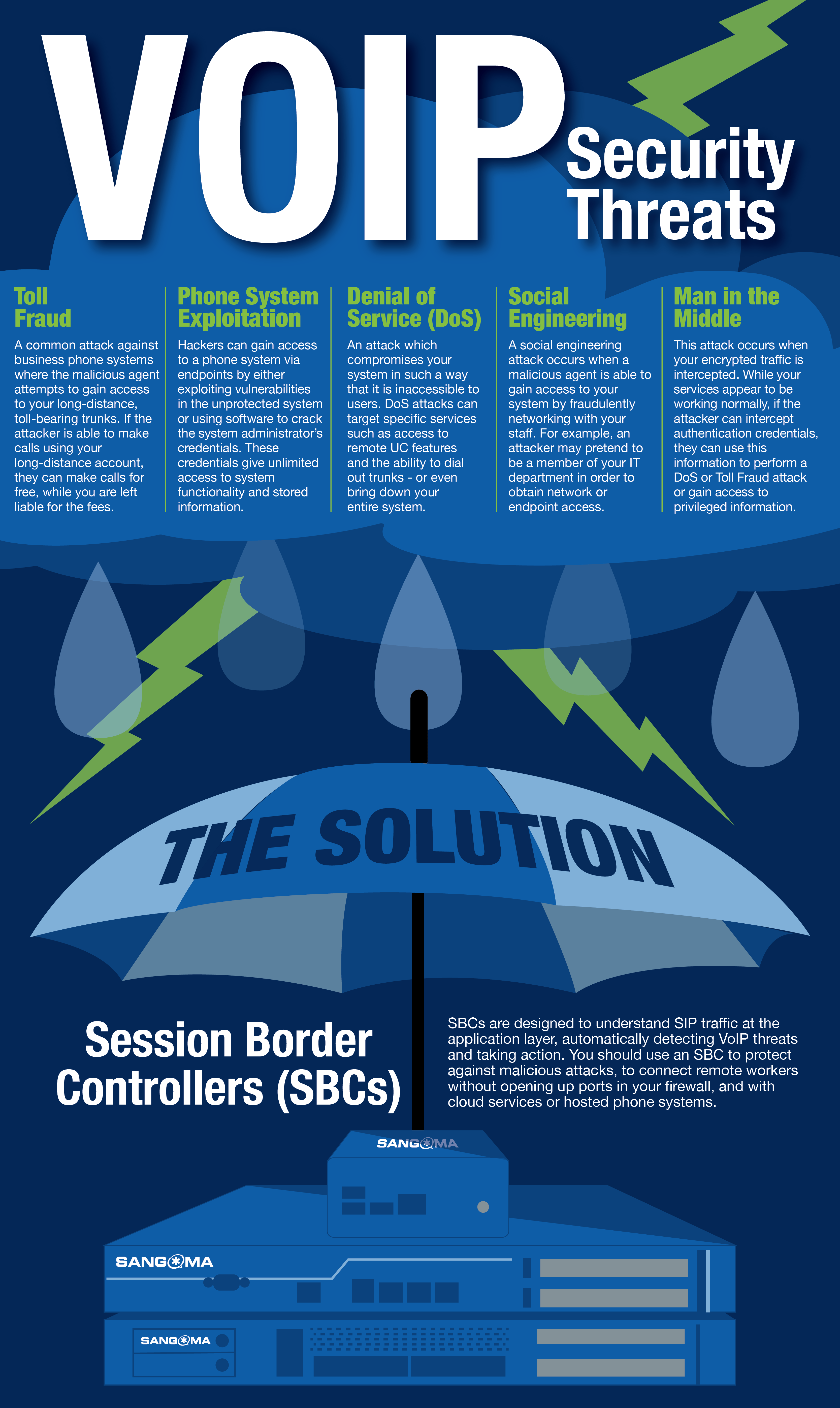
Common VoIP Security Threats
Toll Fraud
A common attack against business phone systems where the malicious agent attempts to gain access to your long-distance, toll-bearing trunks. If the attacker is able to make calls using your long-distance account, they can make calls for free, while you are left liable for the fees.
Phone System Exploitation
Hackers can gain access to a phone system via endpoints by either exploiting vulnerabilities in the unprotected system or using software to crack the system administrator’s credentials. These credentials give unlimited access to system functionality and stored information.
Denial of Service (DoS)
An attack which compromises your system in such a way that it is inaccessible to users. DoS attacks can target specific services such as access to remote UC features and the ability to dial out trunks – or even bring down your entire system.
Social Engineering
A social engineering attack occurs when a malicious agent is able to gain access to your system by fraudulently networking with your staff. For example, an attacker may pretend to be a member of your IT department in order to obtain network or endpoint access.
Man in the Middle
This attack occurs when your encrypted traffic is intercepted. While your services appear to be working normally, if the attacker can intercept authentication credentials, they can use this information to perform a DoS or Toll Fraud attack or gain access to privileged information.
The Solution: Session Border Controllers (SBCs)
SBCs are designed to understand SIP traffic at the application layer, automatically detecting VoIP threats and taking action. You should use an SBC to protect against malicious attacks, to connect remote workers without opening up ports in your firewall, and with cloud services or hosted phone systems.
The post [Infographic] Mitigating Common VoIP Security Threats appeared first on Sangoma.